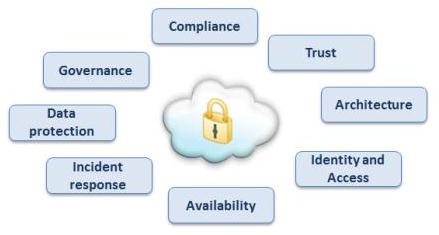
Information about security considerations for cloud computing
Cloud computing refers to the benefit of the savings of the costs and improvement of the outcomes of the business for the organizations. Cloud security is also known as cloud computing security which is in addition to the estimation of the security which is designed to protect the infrastructure based on the cloud, applications, and data. The security considerations for cloud computing give you the applications, and capability of the data, and also provide the management. Cloud security also secures regulatory data which means that keep your data highly secure to the cloud services. This means cloud computing is here to save private data across the online-based infrastructure. Here consists of a variety of information security which is needed to be considered. In addition, it should have ensured that hardware and networks are properly secured.
How does cloud computing work?
The security considerations for cloud computing have many benefits which include the cloud security measures to have works in the following ways:-
- It enables recovery of the data in the case of the loss of the data.
- It protects the storage and also the network which is able to protect it from other frauds.
- It put off the error which is occurring due to the loss of the data.
- It is free from the collision of the data or system compromise.
There are also some of the ways in which security considerations for cloud computing are used for the cloud security works which have benefits and security measures which are written below in the following way:-
Security of the data
It is one of the best features of cloud security which consists of technical things. This includes the barriers in the access and the showing of the data which is having the tools and the technologies. It means there is always the protection of the data if the data is stolen or has been lost. Virtual private networks are also included in the cloud networks which is one of the data protection networks.
Conformity of the legality
It has legal compliance that it has user protection which means having privacy by the legislative bodies. From the danger of exploitation, the exploitation government has taken actions to protect the information of the private user. So many policies and organizations have not been used and they should be banned. Thus, the security considerations for cloud computing have the conformity of legality and legal compliance.
Identity and access management
It means there are some of the accessibilities which are offered by the user accounts. It is here to manage the authentication and authorization of the user accounts is also applied here. There are some things that include multiple authentications, password management, and also other methods. This includes the access controls which are important for many users and are both legitimate and malign.
Planning of the Data Retention and continuity of the business
In this, we can say that if the data has been lost it includes the recovery measures. There are also the plans which are methods of such as backups. In addition, there are many technical systems in which operations can be held which include the testing of the valid part of the backups and also the instructions as valuable through the plan.
Thus these are some of the points by which we are able to get the fact that cloud computing works have many benefits to have works which are written above in the following way.
Some security considerations for the cloud computing
It is always to keep in mind that the security should have to consider the main point to be where it is likely to choose the security provider. The duty of the companies of cloud computing is just to create a safe cloud environment and can also share the responsibility of the security of the data, but further, for the safety, it is just your responsibility. But for network security, the companies of cloud computing are not giving the blueprints the network security. So, you are now more responsible for the safety provider which has addressed cloud computing risks. There are some cloud providers that include security audits, data segmentation, encryption, customer data retention, user data retention, access management, and many more security considerations for cloud computing.
Read More- Windows Live Mail Error 0x8de00005
Risks of the Cloud computing
We have talked about the important works, security considerations, and some other facts about cloud computing. Now we are going to talk about the risks of the security considerations for cloud computing. So, here are some of the risks which include cloud computing which is written below in the following way:-
- Risk of cloud-based infrastructure:- The risk of the infrastructure of cloud-based infrastructure includes conflicting legal frameworks and the third-party storage of the data.
- Internal threats to human error:- It includes the deviation of user access controls.
- External threats:- It gives rise to almost simple such as malware, and many more external threats.
The biggest risk of the security considerations for cloud computing is that there is no perimeter in it. Traditional cyber security is protecting the perimeter but we can say about the cloud environments which are basically connected to the API and there is also a risk of the account which can cause many problems which are faced with the cloud computing security risks to the data-centric approach.
Interrelations can also cause problems. Once the hacker manages to know it they can enlarge and can be able to use the protected interfaces in the cloud to navigate the data on the different databases, they can get into the cloud servers and can even steal the data. This means that security needs to be in the cloud not just to access the cloud data. If the phone network is out of range then you cannot be able to access the data. Third-party data storage can access the threats. These are such examples that you need to look for backups of some of the data and the applications.